The growth of the Internet of Things (IoT) has transformed industries, homes, and critical infrastructure. From connected healthcare devices and industrial automation to smart cities and consumer gadgets, billions of IoT devices are deployed worldwide. With this expansion comes significant security challenges. Attackers exploit weaknesses in devices, networks, and cloud services, making IoT security best practices essential for manufacturers, developers, and system integrators. Hardware reliability, firmware resilience, and software safeguards must work hand in hand with strong pcb design to ensure security at every layer. In this article, we will cover the most important IoT security strategies, real-world threats, and how organizations can adopt a security-first approach.
Why Security is Critical in IoT
IoT devices often operate in environments where a breach can cause serious consequences.
- Healthcare risks: Hacked pacemakers or insulin pumps endanger lives.
- Industrial impact: Manipulated sensors in power plants can lead to outages.
- Consumer risks: Compromised smart locks and cameras threaten privacy and safety.
- Financial damage: Botnets using insecure IoT devices disrupt global networks.
Unlike traditional IT, IoT systems often run on constrained hardware, making traditional security measures difficult to apply. That is why security must be engineered at the device level, starting with hardware and pcb design.
Threat Model: Common Attacks on IoT Devices
To defend IoT systems, one must first understand the attack surface.
- Default credentials and weak authentication: Attackers scan for devices left with factory settings.
- Firmware tampering: Malicious updates or injected code compromise system integrity.
- Physical attacks: Accessing debug ports (like JTAG or UART) to extract secrets.
- Man-in-the-middle attacks: Intercepting unencrypted communication.
- Denial-of-service: Overloading devices with traffic, rendering them useless.
- Supply chain compromise: Malicious components added during manufacturing.
Each of these threats demands specific countermeasures within the IoT security lifecycle.
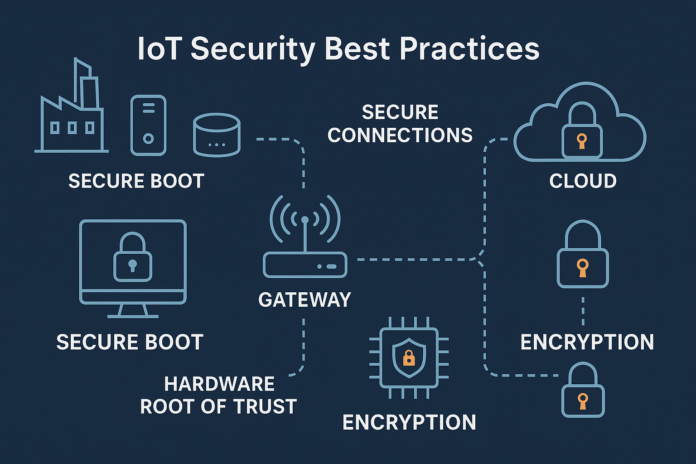
Secure Boot and Hardware Root of Trust
One of the core IoT security best practices is ensuring devices boot only trusted firmware.
- Secure boot: Validates firmware against cryptographic signatures before execution.
- Hardware root of trust (RoT): Embedded hardware modules store keys securely and enforce trust anchors.
- Trusted Platform Module (TPM) or secure elements: Provide hardware-backed cryptography for IoT devices.
By implementing secure boot with hardware RoT, developers prevent malicious firmware from running, ensuring that devices always start from a trusted state.
TLS/SSL and End-to-End Encryption
Data transmitted between IoT devices and cloud servers must remain confidential and tamper-proof.
- TLS/SSL protocols: Secure HTTP and MQTT traffic with encryption.
- Mutual authentication: Devices and servers verify each other before exchanging data.
- Perfect forward secrecy (PFS): Limits data exposure even if keys are compromised.
- Lightweight cryptography: Optimized algorithms for constrained IoT microcontrollers.
Encryption protects against eavesdropping and man-in-the-middle attacks, maintaining user trust and system integrity.
Secure Key Management and Storage
Keys are the foundation of IoT security. Without proper management, even strong encryption can fail.
- Hardware key storage: Use secure elements or trusted execution environments (TEEs).
- Key rotation: Regularly update cryptographic keys to minimize risk.
- Separation of duties: Keys for encryption, authentication, and signing must be distinct.
- Secure provisioning: Keys and certificates should be injected into devices securely during manufacturing.
Strong key management prevents attackers from compromising device identity and communications.
Firmware Update Security (OTA)
Over-the-air (OTA) updates are critical for fixing vulnerabilities, but they also introduce risks.
- Digital signatures: Only signed firmware should be accepted by the device.
- Fail-safe updates: Dual-bank firmware ensures devices can recover if updates fail.
- Encrypted updates: Prevent attackers from analyzing firmware in transit.
- Secure distribution channels: Updates must originate from trusted servers.
Firmware updates are essential for maintaining long-term IoT security, but without proper safeguards, they can become an attack vector.
Protecting Communication Protocols (MQTT, CoAP)
IoT often relies on lightweight protocols that are vulnerable if left unsecured.
- MQTT: Must be used with TLS for encryption and authentication.
- CoAP (Constrained Application Protocol): Should employ DTLS (Datagram TLS) for secure communication.
- Access control: Limit which devices can publish or subscribe to topics.
- Rate limiting: Prevent denial-of-service attacks by controlling message frequency.
Securing communication protocols ensures reliable and private data exchange in IoT ecosystems.
Physical Security for IoT Devices
Even the strongest encryption cannot protect devices from direct physical tampering.
- Disabling debug ports: Remove or secure UART/JTAG access on production boards.
- Tamper detection sensors: Alert systems when unauthorized access occurs.
- Epoxy potting and conformal coating: Make reverse engineering more difficult.
- PCB-level design for security: Shield sensitive traces and use secure storage chips.
Physical protections combined with strong pcb design can significantly reduce hardware-based attacks.

Privacy and Data Protection Considerations
Security extends beyond devices to the data they handle.
- Data minimization: Collect only what is necessary.
- Anonymization: Remove identifiers before storing or transmitting sensitive data.
- Compliance with regulations: GDPR, HIPAA, and other laws demand strict handling of personal data.
- User transparency: Provide users with clear consent and data usage policies.
Balancing IoT functionality with user privacy is a key challenge in secure design.
Certification Standards (UL, ETSI EN 303 645)
Adhering to industry standards builds trust and ensures compliance.
- ETSI EN 303 645: Baseline security for consumer IoT devices.
- UL 2900: Safety and cybersecurity standard for network-connected products.
- NIST IoT guidelines: Best practices for manufacturers and developers.
- ISO/IEC 27001: Broad information security management standards.
Certification ensures products meet recognized security benchmarks and provides customers with confidence in IoT solutions.
Building a Security-by-Design Culture
Security cannot be added after the fact; it must be built into IoT products from day one.
- Threat modeling during pcb design: Anticipate potential attack vectors at hardware level.
- Code reviews and static analysis: Detect vulnerabilities early.
- Penetration testing: Simulate real-world attacks before product launch.
- Training and awareness: Ensure engineers prioritize security alongside functionality.
Organizations that adopt a security-first culture reduce risks and build products that can withstand evolving threats.
Conclusion
The rise of IoT brings both innovation and risk. Implementing IoT security best practices is essential for protecting users, devices, and networks. From secure boot and encryption to OTA updates and certification, every layer of IoT architecture must be protected. Just as strong pcb design ensures hardware reliability, strong security practices ensure devices remain trustworthy. By adopting a security-by-design culture, organizations can deliver IoT products that meet customer expectations, regulatory requirements, and long-term reliability goals.