A modern device is never finished. Users expect fixes and features after install day, regulators demand security patches, and product teams push rapid improvements. That reality makes Firmware over-the-air (OTA) updates a first-class requirement, not an afterthought. This article lays out a practical, end-to-end view: architectures (dual-bank, A/B), cryptography and signing, delta vs full images, rate limiting and resume, validation and rollback, and the operational muscle to run rollouts at scale. If your pcb design ends up in vehicles, buildings, factories, or homes, the following choices will decide whether updates are smooth or scary.
Why OTA updates are critical
OTA is the only viable path to keep fleets current when devices are remote or sealed. It cuts truck rolls, closes vulnerabilities quickly, and enables paid features after shipment. For hardware startups, OTA shortens feedback loops: instrument the fleet, ship small changes often, and learn what real users need. For regulated sectors (medical, utility, automotive), OTA is part of the safety story—timely fixes reduce field risk and total liability. OTA also affects manufacturing: the first firmware flashed at the factory can be minimal, with calibration data and secure keys provisioned, then a production image pushed on first boot. That simplifies lines and helps you ship boards earlier.
The moving parts of an OTA system
A workable OTA stack has a few clear pieces: 1) Artifact build: reproducible toolchains produce versioned binaries; symbols and debug info are archived. 2) Signing pipeline: a dedicated service signs release artifacts with a private key kept in an HSM or a sealed vault; the device has the corresponding public key. 3) Distribution: a broker (MQTT), API, or CDN serving static files delivers updates; large fleets benefit from caching gateways. 4) Device agent: authenticates the server, checks policy, downloads with resume, verifies signatures and checksums, writes to inactive memory, and coordinates reboot. 5) Orchestrator: rollout waves, percentage ramps, targeting by hardware revision or geography, and kill switches. 6) Observability: cohort stats, success/failure reasons, median download times, and power-event correlations.
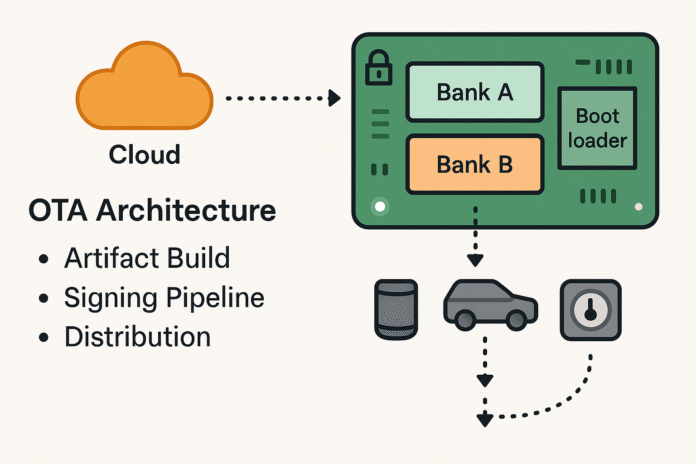
Bootloaders and dual-bank architecture
The most dependable pattern is dual-bank (A/B) flash with an always-on bootloader: • Bootloader: tiny, read-only, and signed at manufacturing; it never updates in the field unless you have a safe field-upgrade plan for it. It decides which bank to boot and contains the crypto to verify images before handoff. • Bank A / Bank B: one active, one staging. The device downloads into the staging bank, validates, marks “pending,” and reboots. If the OS/app sends a health heartbeat within a trial window (e.g., 30–120 s), the bootloader marks the new bank as “good.” Otherwise it rolls back to the previous image automatically. • Settings partition: stores version, flags, and monotonic counters separate from app data, ideally with a small wear-leveling scheme. • Watchdog: runs during both download and trial boot; the bootloader and new image must both prove liveness. Benefits: almost no “bricking,” safe power-loss behavior, and quick rollbacks that don’t require cloud reachability.
Single-bank with swap (when flash is tight)
If you don’t have room for two full images, a swap scheme copies chunks between app and scratch partitions. It’s more complex and power-loss sensitive; use a journaled state machine and CRC at each step. Test power cuts every few hundred milliseconds during swap on real hardware before shipping.
Secure OTA frameworks
Security sits at the heart of OTA. The device must accept only authentic images and the backend must apply least-privilege rules. A robust approach uses: • Public-key signatures on the artifact manifest; devices verify with a public key burned at manufacture. • Hash trees or signed manifests that list component images (boot, kernel, app, model files) with digests and sizes. • Key rotation: devices store a keyring; the manifest can roll the signing key under quorum policies. • Version monotonicity: prevent downgrade to known-bad builds unless a signed rescue manifest explicitly allows it. • Time checks: guard against replay; if your device has no RTC, use monotonic counters rather than absolute time for the acceptance policy. If you run Linux, package managers such as swupdate, RAUC, Mender, or OSTree apply these ideas; on RTOS/MCU, a small manifest and X25519/Ed25519 crypto fit well.
Versioning and rollback mechanisms
Use semantic versioning with hardware qualifiers: app-2.7.1+hwA vs app-2.7.1+hwB if pinouts or PMIC timings differ. Devices report current, staged, bootcount, and last-fail-reason. The orchestrator rolls forward or back by cohort. Rollbacks should be automatic after a health window if no heartbeat arrives. For staged rollouts, allow an override: engineers can force “stick on new” for lab units even if the heartbeat is late.
Delta vs full firmware updates
Full image updates are simple and robust; the device writes a single signed blob to the staging bank. The cost is bandwidth and flash cycles. Delta (binary diff) updates shrink downloads dramatically by sending only changed regions. Worth it when images are large, links are slow, or carriers bill by byte. Trade-offs: 1) Both base and target images must be known; the device must prove its current version before applying the patch. 2) Patch application increases CPU time and power draw. 3) If either side mismatches, you need a fallback to a full image. Practical advice: start with full images for your first product cycle; switch to deltas once your fleet passes 5–10k devices or your payloads exceed a few megabytes and you have stable baselines.
Handling intermittent connectivity
OTA lives in the real world: weak Wi-Fi, dead zones, mesh links, and cellular caps. Patterns that work: • Resumable downloads with content-range and strong checksums per chunk; store progress in the settings partition every N kilobytes. • Backoff and jitter to prevent thundering herds when gateways restart. • Windowed rollouts: schedule firmware pulls at quiet hours per region to avoid competing with user traffic. • Compression: LZMA or heatshrink-style streaming across chunks. • Bandwidth caps: per-device and per-gateway to stay under carrier plans. • Local fan-out: one device in a site downloads the image; nearby devices fetch over LAN with mutual TLS. • Power awareness: on battery devices, postpone large downloads until SoC > 50% or charger present; on energy-harvested nodes, use a budget scheduler that downloads a limited number of chunks per wake cycle.
Encryption and authentication for updates
Transport security (TLS) keeps the channel private, but device safety depends on artifact authenticity. Mandatory steps: • Sign the artifact with an offline private key; verify in the bootloader before any execution. • Pin the CA or server public key for device-to-cloud auth; avoid trusting the system store alone. • Mutual TLS with device certificates prevents rogue clients from scraping your artifact bucket. • Per-device tokens limit blast radius if one unit leaks credentials. • Encrypt at rest: not required if signatures are enforced, but encrypted payloads keep reverse-engineering harder when devices are widely distributed. Store keys in a secure element when possible.
Testing and validation of OTA processes
Updating flawlessly in the lab means little unless it survives chaos. Build a lab rig that power-cycles devices at random during each OTA phase. Script hundreds of power cuts while swapping banks to prove idempotence. Add packet loss emulation and rate limiting to mimic the field. Validate these cases: • Download interrupted and resumed. • Manifest rejected (bad signature, wrong hardware). • Image verified but heartbeat never received. • Rollback from new app to previous app. • Mass-erase fallback after repeated failures. • Bootloader update path disabled or protected. Keep a golden device with write-protected flash to confirm your signing keys and acceptance logic. For Linux or Zephyr builds, run OTA in CI on real hardware using USB relays for power and a simple RF shield box for radios. Track pass/fail per commit and publish a table to the team.
Cloud-based vs local OTA management
Cloud-managed OTA (SaaS or your own service) scales across fleets and geographies with dashboards, cohorts, AB tests, and APIs. Advantages: global CDNs, auth, and audit logs are solved. Risks: vendor lock-in; plan data export and a migration path. Local OTA (on-prem or gateway-based) works in disconnected facilities (oil & gas, ships, mines, defense). Gateways receive signed updates occasionally and fan them out over LAN or a private mesh. Hybrids are common: the cloud plans rollouts and gateways handle last-mile delivery. For consumer gear, mobile apps often act as proxies: the phone downloads the artifact over broadband and relays it to the device over BLE or Wi-Fi Direct with checksum and signature checks on both sides.
Case studies of OTA failures
Power loss during swap: a smart meter bricked because the swap state machine didn’t journal progress; a mid-swap brownout corrupted both banks. Fix: chunked copy with a monotonic step counter; verify each page before erase/write of the next. DNS outage at a CDN: devices rebooted midway through downloads and retried too quickly, DoS’ing the resolver. Fix: exponential backoff with jitter and cached alternative endpoints. Expired signing certificate: a team forgot that manifests include a signing cert with an expiry; devices rejected a valid image. Fix: store long-lived root keys on devices and rotate intermediates proactively; add CI checks that fail a build if expiry is < 180 days. Stuck on new version: the new app had a logging loop that serviced the watchdog; the heartbeat to the bootloader never fired. Devices didn’t roll back. Fix: make the heartbeat independent of application loops (e.g., a bootloader-monitored shared flag toggled by a minimal task). Wrong hardware cohort: a PMIC timing change for HW-B broke startup on HW-A boards shipped earlier. Fix: target by hardware revision plus serial range, and read the board ID from OTP in the acceptance gate.
Designing for scalability
Think in cohorts and levers: Cohorts: group devices by hardware revision, geography, carrier, firmware major version, and customer. Rollout waves: 1% → 5% → 20% → 100% with gates between steps; gates check failure rate, time to first heartbeat, and post-update crash rates. Rate limits: cap concurrent downloads per region so your backend and carriers stay healthy. Observability: capture reasons for failure as enumerations (DNS, TLS, 401, low battery, no space, CRC fail, heartbeat timeout, user canceled). Storage budget: design with at least 2× image size + settings + logs; on NAND, add wear-leveling and bad block handling. Edge caching: for campuses and factories, a local cache reduces head-end costs by orders of magnitude.
Practical memory maps and file systems
Flash is unforgiving. Consider: • Align partitions to erase boundaries. • Use a robust file system where appropriate: littlefs on NOR; UBIFS on NAND; advantages include power-loss safety and wear leveling. • Protect the bootloader with read-out and write-protect bits; expose an RMA unlock path through authenticated service tools. • Add a scratch area for swap or delta decompression. • Cal/keys live in a small, redundant partition with checksum and a monotonic counter to prevent rollback.
Power and thermal behavior
OTA often means sustained radios and flash writes. On battery products, updates can be the biggest energy event of the month. Tips: • Require external power or a minimum SoC before starting. • Throttle CPUs during decompression/delta apply to stay in thermal bounds. • Drop to a low-rate logger to avoid wearing the flash with excessive logs during a long update. • Store a resume token every minute so even a power cut late in the download avoids starting over.
Human factors and UX
For consumer products, OTA is a user experience: • Announce the update with clear text, duration estimate, and benefits. • Offer a “defer” option and a window. • Blink LEDs or show an on-screen progress bar. • On devices without screens, expose progress through the companion app. • After success, show a simple “Updated to X.Y.Z” message with a link to release notes. For industrial devices, the “user” is a technician: put short status codes on a seven-segment or expose them over a service UART/BLE. A laminated card with error codes speeds field work.
OTA for RTOS and bare-metal MCUs
Even tiny MCUs can do OTA with a lean agent: • Use chunked downloads over BLE, LoRaWAN, or a narrowband modem; sizes of 128–512 bytes are common. • Verify each chunk’s hash and store to staging flash. • After commit, verify the full image’s signature in the bootloader before jump. • For LoRa/mesh, throttle to duty-cycle limits and expect multi-hour updates; design for resume across days. • Keep the bootloader able to accept a local update (wired UART/SWD) for rescue.
OTA for Linux and containerized systems
On larger SoCs, you might update a kernel, rootfs, and apps. Patterns: • A/B rootfs with verified boot (dm-verity). • RAUC/mender/swupdate handle signed bundles, post-install scripts, and rollback. • Containers: for app code, pull signed images; keep the base OS update separate so failures in app layers don’t touch the boot path. • Atomicity: flips a bootloader variable only after bundles verify, then rolls back on failure to boot within a health window.
Data models and manifests
A clean manifest makes the device agent small and the policy flexible. Include: product identifier, hardware revision, target version, supported upgrade path(s), component list (with sizes and SHA-256), signature block, minimum battery level, minimum free space, and reboot policy. Optional fields: time windows, geofence hints, and canary cohort rules. Keep the parser strict and well-tested; malformed manifest should abort early with a clear reason.
Observability: what to measure
Per cohort, track: request count, download starts, chunk retries, resume events, median and p95 download time, verification failures, boots to “good,” rollbacks, and time to heartbeat. Correlate with power events, radio RSSI, and carriers. A small reason code taxonomy (dozens, not hundreds) helps product and ops spot patterns quickly. Export metrics to dashboards your on-call team actually watches.
Compliance and safety notes
In regulated sectors, record software of unknown provenance elimination steps, signing keys custody, and audit logs of who approves a rollout. Keep release notes with CVE references. If a device has safety-related functions, restrict OTA to windows when actuators are idle and make the bootloader drop outputs to a safe state before reboot. For some markets, you must keep update servers in specific regions; plan CDN buckets accordingly.
A hands-on rollout playbook
- Build the artifact; store symbols and a manifest. 2) Sign in CI; publish to a staging bucket. 3) Canary to 1% of the fleet (lab + friendly users). 4) Wait for success thresholds (e.g., >98% reach “good” within 10 minutes). 5) Roll to 5%, then 20%, then 100%, with a kill switch ready. 6) If failures rise, freeze the wave, analyze reason codes, and push a rollback manifest. 7) After completion, archive metrics and artifacts; link to the release notes in your issue tracker.
Manufacturing and first-boot
Provision secure keys and serials at the line; store them in OTP or a secure element. Flash a minimal factory image with a bootstrap agent, then let the device fetch the latest stable on first power in the field. That decouples the line from release cadence and reduces rework when software changes late.
Cost modeling
Bandwidth and backend costs scale with bytes and concurrency. A rough rule: for a 5 MB delta every two weeks and a 50k fleet, budget tens of gigabytes per day during ramps; place caches near large customers. Storage for artifacts and logs grows quickly; lifecycle policies that expire old deltas when their base falls out of service will keep bills reasonable.
Common mistakes to avoid
• Treating OTA as “just a URL” instead of a signed workflow. • No automatic rollback. • Putting crypto only in the application, not the bootloader. • Assuming time is available for certificate checks when the device has no RTC. • Skipping brownout tests. • Leaving debug logs at high verbosity and wearing out flash. • Forgetting that option bytes or device tree changes can affect boot time relative to your heartbeat window.
Conclusion
A dependable OTA system is both a design pattern and an operational habit. At the device level, keep a small, trusted bootloader, dual banks, signed manifests, and an automatic rollback with a clear health signal. On the network side, use resumable downloads, rate limiting, gateways that cache, and metrics that tell you when to pause. In the cloud, treat signing keys as crown jewels and throttle rollouts by cohort. Do these consistently and Firmware over-the-air (OTA) updates become routine rather than tense. Your teams will ship fixes faster, your customers will notice improved reliability, and your fleet will stay safer for years.